Cyber Security Insurance: Ransomware Payments Average up 43%
Plan Your Risk Management Strategy
An oft-overused quote by me is "I skate to where the puck is going, not where it has been" (Wayne Gretzky). Like hockey, cyber security is fast-paced, violent and can leave one pretty roughed up if not aware. Blood spills, and in this game, the refs are non-existent. These facts proven out below by our friends from Carrier Management in its entirety.
- Average payment for ransomware attacks up 43% ($154,108 v $220,298). Any holiday cheer in Q4 2020 went out the window in Q1 2021 and limits should be reviewed accordingly
- Median payments on claims up 58% ($73,398 v $49,450)
- Average downtime due to ransomware in Q3 2019 - 12 days and in Q3 2020 - 19 days; pay attention to the oft-neglected "Business Interruption Worksheet" to set proper limits and deductibles based on your specific exposure if down.
- "The biggest change over the six quarters ending Q3 2020 was that threat actors had come to “realize that their tactics scale to much larger enterprises without much of an increase in their own operating costs.” In other words, “the profit margins are extremely high, and the risk is low,” Larger companies are more lucrative targets and usually cost the same/have same risks to breach. Be even more concerned with size and ability to pay the ransom. They know what you can spend as they have all your files.
- Plan your risk management strategy yesterday and your renewal today. Do not wait until your normal cyber anniversary date to understand your exposures and address them prior to your renewal. The cost to address concerns will probably be paid for just in the reduction of premium to mitigate threats
...keep your head on a swivel on this front. Barriers of entry for the bad folks are low, rewards are high and prosecution very tough due to anonymity and global nature of the crime.
I look forward to visiting the "City of Lightning" for the next few days for the NAPEO CFO Conference and hope to see you there!
The Ransomware Epidemic by the Numbers

During a session of the Casualty Actuarial Society Seminar on Reinsurance in June, Alexander Podmore, AVP and cyber underwriter for Swiss Re, defined a growing problem for cyber insurers—ransomware—and shared some data to underscore just how bad things are getting.Cyber Underwriting Changes: Is It Too Little Too Late?”
Ransomware is a form of malware that enters an insured’s network causing an encryption of data and systems, rendering them unusable until the victim restores their data and systems from backups, and incurs the relevant business interruption costs, or the victim pays a ransom demand to the hacker to provide safe return of the encryption key to restore access to the data and systems.
Citing figures from the latest quarterly report of Coveware, a firm that helps businesses remediate ransomware, Podmore noted that the average ransom payment in first-quarter 2021 was just shy of $250,000, having risen from “the low hundreds of dollars” in third-quarter 2018. In the space of two years, there has been an exponential increase, he said.
Below are some other figures and highlights from recent Coveware reports.
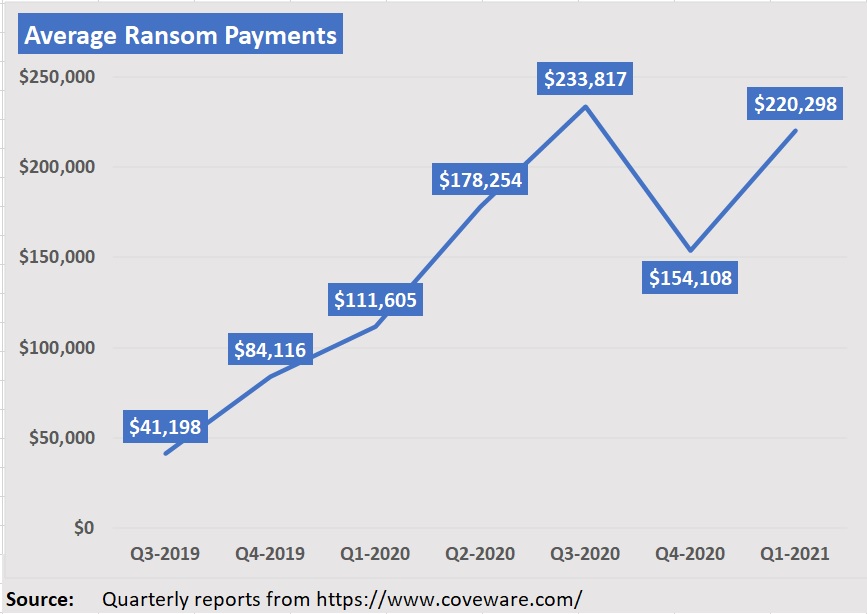
- After a temporary decline in fourth-quarter 2020, the average ransom payment increased 43 percent to $220,298 in Q1 2021 (from $154,108 in Q42020). Compared to the Q1 2020 quarter a year earlier, the Q1 2021 average payment has almost doubled.
- Q1 2021 averages were pulled up by a raft of data exfiltration attacks by one specific group.
- The median payment in Q1 jumped to $78,398 from $49,450, a 58 percent increase.
- Temporary declines in average and median payouts in Q3 2020, according to Coveware, were the result of the fact that while ransomware groups continued to leverage data exfiltration as a tactic, the trust that stolen data would be deleted was eroding. Exfiltrated data continued to be made public despite victims paying ransom.
- In Q4 2020, email phishing overtook RDP compromises as the dominant attack vector for the first quarter since Coveware had been tracking data. In Q1 2021, RDP compromise was predominant again, but the gap between the two types of compromises was smaller than in past years.
- Incident duration expanded slightly in Q1 2021 to an average of 23 days. The downtime measure has been creeping up, with prior reports showing 21 days in Q4 2020, 19 days in Q3 2020.
- In Q4 of 2019, average downtime increased to 16 days from 12 days in Q3 2019. Coveware said the increase in downtime was driven by a higher prevalence of attacks against larger enterprises, who often spend weeks fully remediating and restoring their systems.
- Commenting on the highest level reported in recent quarters, in Q3 2020, Coveware said that “attackers discovered that the same tactics, techniques and procedures that work on a 500-person company can work on a 50,000-person company, and the potential payoff is substantially higher.”
- The biggest change over the six quarters ending Q3 2020 was that threat actors had come to “realize that their tactics scale to much larger enterprises without much of an increase in their own operating costs.” In other words, “the profit margins are extremely high, and the risk is low,” the Q3 2020 report said.
Sources: Quarterly reports from https://www.coveware.com/
Q1 2021: Ransomware Attack Vectors Shift as New Software Vulnerability Exploits Abound
Q4 2020: Ransomware Payments Decline in Q4 2020
Q3 2020: Q3 Ransomware Demands Rise: Maze Sunsets & Ryuk Returns
Q2 2020: Ransomware Attacks Split Between Enterprise & RaaS
Q1 2020: Ransomware Payments Up 33% in Q1 2020
Q4 2019: Ransomware Costs Double in Q4 as Ryuk Sodinokibi Proliferate
(Coveware: Ransomware Recovery First Responders)
In several of the quarterly reports, Coveware notes that although victims may decide there are valid reasons to pay to prevent the public sharing of stolen data, Coveware’s policy is to advise victims of data exfiltration extortion to expect that even if they opt to pay:
- The data will not be credibly deleted. Victims should assume it will be traded to other threat actors, sold or held for a second/future extortion attempt.
- Stolen data custody was held by multiple parties and not secured. Even if the threat actor deletes a volume of data following a payment, other parties that had access to it may have made copies so that they can extort the victim in the future.
- The data may get posted anyway by mistake or on purpose before a victim can even respond to an extortion attempt.
Join the Conversation on Linkedin | About PEO Compass
Contact Professional Employer Organization (PEO) Expert, Paul Hughes
Paul Hughes has been working with the Professional Employer Organization (“PEO”) industry since 1995 and data management since 2005. He is responsible for the day to day operations of both Libertate Insurance Services, LLC and RiskMD, which reports into the overall Ballator Insurance Group family of companies. Learn more about Paul.
Specializing in PEO Services: Workers Compensation, Mergers & Acquisitions, Data Management, Insurance Focus on: Employment Practices Liability (EPLI), Cyber Liability, Health Insurance, Occupational Accident, Business Insurance, Client Company, Casualty, and Disability Insurance.

